|
|
|
|
Products . Stealth Storage |
Sign In |
|
Protect your personal data on notebook computer
Have you ever thought what happen if you lose your notebook computer?
All your documents, images, videos can be easyly read by evil-wisher.
Even your emails can be read!
We offer a solution that completely protects your computer
Our Stealth Storage system will transparently encrypt all your private data using strong cipher algorithms.
Unlike other programs, Stealth Storage never keeps plain data on your hard disk.
Your private files remain encrypted even if your computer is suddenly turned off!
The desktop computer can be protected as well. No special knowledge required in order to start using Stealth Storage.
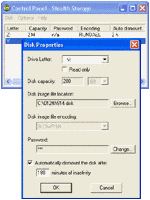
How does Stealth Storage work
Stealth Storage mounts a disk to your system, so all the software (including Windows itself) thinks you have one more hard disk.
All requests to files stored on hard disk are encrypted and decrypted on-the-fly.
Disk image is a regular file stored on your hard drive. You can copy, delete, move and backup it like you do it with other files.
Password is required in order to mound a disk. You can assign any drive letter to the disk (D:, E: etc).
Why you should use Stealth Storage
There are many similar programs on the market.
But our software is completely different. Below we outlined the most significant differences.
- Stealth Storage software is stealth. It does not have any graphical user interface (except configuration window, though). Nobody will even know you are running Stealth Storage.
It even does not have a window where you must type a password! You can do it in any other program, for example in MS Word, or Notepad.
So, even a person who sits behind you, will not notice you mounted a disk!
- Stealth Storage will automatically dismount encrypted drives due to inactivity. This is useful feature if you leave your computer alone for some reason. Our software will take care about this possible security leak and dismount a disk if you do not use it for a while.
- Stealth Storage can run programs after disk is mounted and before one is dismounted. For example, Outlook Express can be run automatically after you mount a disk, if you store OE database on encrypted disk.
- Stealth Storage is very small. It uses very little system resources.
- Many strong ciphers are supported: IDEA, CAST, 3WAY, BLOWFISH, RIJNDAEL, TWOFISH
|
| mobile version |
Copyright © 1999-2026 SoftCab, Inc. All Rights Reserved · |